Secure Programming for the WWW
1 Purpose
The purpose of this assignment is to help you
understand the kinds of defects that lead to vulnerable "web apps"
and how to avoid, detect, and eliminate them.
Specifically, by the time you complete this
assignment you should understand vulnerabilities that can lead to:
- Local HTML Injections
- Reflected HTML Injections
- Local Cross-Site Scripts
- Reflected Cross-Site Scripts
2 Overview
This assignment has two closely-related parts. For part 1 you will
attack two versions of a WWW site (one with a local vulnerability
and one with a reflected vulnerability) and for part 2 you will
eliminate those vulnerabilities.
The WWW site you will be attacking and correcting is for a
fictitious company named Trusted Travel. Their home page contains
some contact information and some links to information about cities
around the world. they use the query string in the URL to transmit
information about the various affiliates that they work with.
The version of the site that contains a client-side (i.e., local)
vulnerability is available at:
and the version of the site that contains a server-side (i.e., reflected)
vulnerability is available at:
(Note: If you load the
.html version
of the page with
the server-side vulnerability you will be able to view the PHP
source code.)
3 Requirements of the Attacks
You must complete several different attack-related tasks.
-
You must create two HTML pages that can be used to conduct a
cross-site script attack (using a JavaScript injection) against the
two vulnerable pages (i.e., you must create one HTML page that can
be used to mount an attack against one of the vulnerable pages, and
another HTML page that can be used to mount an attack against the
other vulnerable page). The pages must appear to be trustworthy but
must, in fact, change all of the links on the Trusted Travel page so
that they refer to a page on your site. The malicious code must not
impersonate the vulnerable page (which could be accomplished with
just HTML/CSS), it must modify the vulnerable page (which will require the
use of JavaScript).
-
You must create two HTML pages that can be used to conduct
an HTML injection attack against the two vulnerable pages. The pages
must appear to be trustworthy but must, in fact, pop-up a password
dialog on the Trusted Travel page that looks like the following:
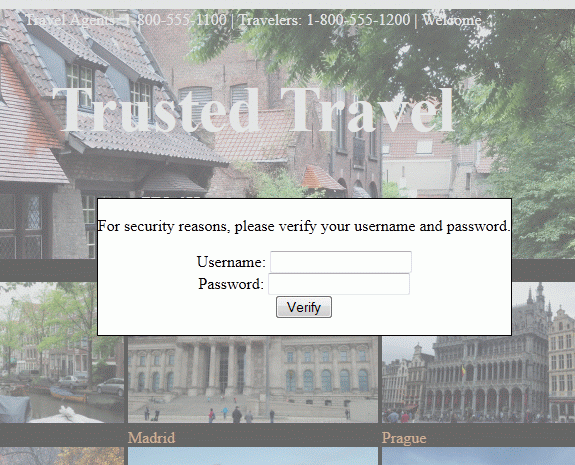
Note that the Trusted Travel page must be "grayed-out" and it must
not be possible for the user to click on any of the links on the
page. (Hint: This can be accomplished in HTML/CSS using
two div elements, one that covers the whole page and
one that contains the password dialog.) Note also that the password
field must be an input
of type
password so that it is less suspicious.
Note finally that when the Verify button is clicked, the
username and password information must be POSTed to a page on your site.
-
The links on the four pages above might look suspicious to some
users. Hence, to make your attack more likely to succeed, you must
create WWW pages that use redirection to conceal the suspicious
links. (Hint: There are several ways to redirect a WWW browser to
another page. Read about them and then use the one that you think
will be least suspicious.)
4 Requirements of the Mitigations
You must create versions of the two vulnerable pages that
eliminate the vulnerabilities without changing their desired functionality
(i.e., they must include the ability to display affiliate information in the
welcome message at the top of the page). Note that your solution must be
as easy to administer as possible (since Trusted Travel adds affiliates
very frequently).
5 A Note About Tools
Several browsers now include XSS "filters" that attempt to mitigate against
XSS-related attacks. They do not work very well, but they do work well enough
to be inconvenient for this kind of exercise.
You may be able to deactivate the filter to test your attacks.
Internet Explorer: Tools-Internet Options-Security-Custom and select
"Disable" under "Enable XSS Filter".
Firefox: Enter "about:config" in the URL bar and search for
"browser.urlbar.filter.javascript" and double-click on it to set it
to false.
Chrome: Start Chrome from the command-line using the switches
-args --disable-xss-auditor.
You will probably need to re-start the browser for the changes to take
effect.
Remember to reactiavte the filter when you are done to reduce your chances
of falling victim to any actual attacks.
If all else fails, you can install a version of the trusted site on
stu (or your local machine) and attack that version
rather than the one on this server (since then all of the scripts
will be coming from the same server and the filters won't
object). The files you need are in
trusted.zip. Of course, you must not modify
these files in any way.
6 Submission
You must submit the following.
- A
.zip file containing all of the HTML/CSS/JavaScript/PHP
files you created for this assignment, organized appropriately.
- A "paper-like" document that contains instructions for using
the attacks that you created and for using the invulnerable versions
that you created.
- A "paper-like" document that contains a description of the
different mitigation techniques you considered, their advantages and
disadvantages, and the alternative you chose to implement.
- A "paper-like" document that contains a description of the
different ways to redirect a WWW browser to a different page and the
advantages and disadvantages of each from an attacker's perspective.
7 Visibility
Your deliverable will be public (i.e., available to both other students
in the course and the general population).

